The scale of cyberattacks steadily grows and often goes undetected. Cybercriminals use the internet infrastructure to attack and hide behind anonymity to carry out their crimes. How are we to respond to increasing cyberattacks and cybercrime? It is a fundamental question.
Security analysts need a real time unique intelligence about related domains, IP addresses and queries to thoroughly study, analyze the information and quickly remediate threats before they cause substantial harm.
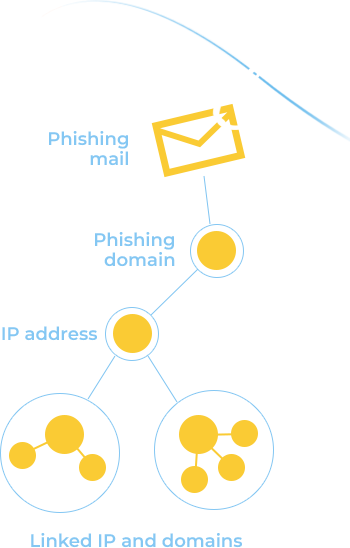
Studying passive DNS data allows researchers to track which domain names are hosted by particular name servers and which domain names point to which IP networks, identify anomalies and detect changes in DNS resolving on interested domains.
Passive DNS historical data also allows security teams to detect patterns of malicious activity, identify phishing and other targeted attacks.
Octopus, a SafeDNS analytical and threat intelligence system builds and presents the data in a convenient form accumulated from:
15 nodes around the world, >1B DNS requests processed daily
Based on machine learning to detect malicious sites and categorize internet resources, 180M domains in web crawler index
1.2B records up-to-date
Armed with Octopus, analysts, researchers, SOCs, and security teams can:
Speed up neutralization of incidents and investigations by automating analysis processes
Identify all IP addresses a cybercriminal is using to conceal malicious activity
Identify who is behind the attacks and create a fingerprint of cyberattackers’ network
Uncover all domains using the same name server infrastructure used by a detected "bad" domain
Automate the analysis of existing processes using RESTful Octopus API
Reveal connection between the sources of threats to track and block their activity